CHECKPOINT + CYSIGHT
AI-DRIVEN UNIFIED CYBER SECURITY
BENEFITS
- Provides an integrated security monitoring, performance management, and capacity planning environment for SOC and NOC teams.
- Single solution for Anomaly Detection, Forensics, Threat Intelligence, Root cause Zero Trust and Network/Cloud Accountability.
- Eliminates visibility blind spots and is not constrained by granularity limitations.
- Collects, tags, retains, and correlates network and cloud flows and application metadata to identify cyber-threats that would otherwise be undetectable using predictive AI.
- Anomaly detection, security forensics and performance monitoring to highlight hidden anomalies.
- Perpetual diagnostics detect spurious traffic from Infiltration, Exfiltration, DDoS attacks, P2P abuse and insider threats.
- End-Point threat intelligence identifies Ransomware, botnets, hackers, traders in illicit material, or other known bad actors.
- Complete drilldown forensics into suspect communications.
- Easy to deploy, easy to use.
- Highly automated: requires a low labor effort to manage and maintain.
- Granular, scalable, and actionable intelligence about everything traversing your network.
INSIGHTS
Enterprises face significant visibility issues to properly safeguard their network and cloud connected digital assets in the age of encryption. These challenges encompass Cyber Threats, Encryption Complexities, Visibility Gaps, Applications Intelligence, Compliance and Looming Risks. Organizations need reliable and real-time diagnostics, network analysis and performance monitoring to enhance the effectiveness of their existing security strategies.
JOINT SOLUTION
Check Point and CySight have partnered to enable enterprises to have uncompromised protection against all types of threats, real-time qualification, granular historical visibility of all traffic flows recorded for enhanced security forensics, compliance, trending, alerting and automated traffic diagnostics.
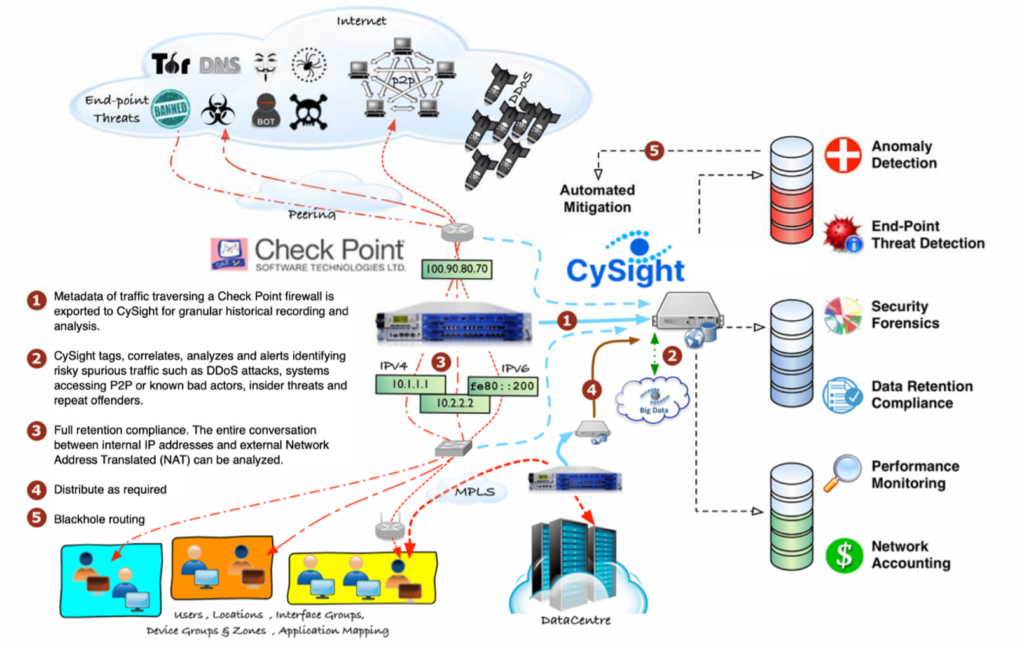
Check Point’s fined-grained packet-based access control and enriched metadata, coupled with CySight’s granular real-time detection and long-term security surveillance provide an enhanced security solution with complete visibility into suspect communications and connects the dots between internal IP addresses and external Network Address Translated (NAT) conversations substantially strengthening the ability to defend your digital assets.
CySight’s Integrated AI-Driven Network Detection and Response (NDR) and Endpoint Detection and Response (EDR) with Predictive AI Multi-Dimensional Baselines and Threat Intelligence Correlation technology analyzes flow records in real-time and uses machine learning making use of historical data trends and threat intelligence to identify risky spurious traffic such as DDoS attacks, Ransomware, P2P abuse and insider threats, and to mitigate security threats that would otherwise be hidden.
CySight’s measurements provide engineers clear analytics to completely understand their traffic flows enabling access lists to be more clearly checked or monitored when access has been discontinued enabling unnecessary rules to be removed maintaining Check Point firewall efficiency. Application, Threat, Country, and Asset Intelligence make it easy to identify traffic ownership and risk.
CySight constantly monitors your network traffic and provides total visibility to quickly identify and alert on who did what, where, when, with whom and for how long. Led by a smart network predictive AI baselining solution CySight continues to generate actionable insight by delivering the right monitoring information to the right teams at the right time.
Check Point amplifies CySight’s AI and Forensic capabilities to enable swift identification of Cyber Threats concealed within encrypted traffic. CySight ingests Enriched flow metadata from Check Point’s firewalls and uses machine learning to detect change impacting hosts and services with total visibility, flexibility, and granularity. CySight ingests Check Point’s enriched environment context to provide easy visibility and Zero Trust management and identifies key issues that can then be automatically mitigated by Check Point.
ABOUT CHECK POINT
Check Point Software Technologies Ltd. (www.checkpoint.com) is the largest pure-play security vendor globally that provides industry-leading solutions and protects customers from cyberattacks with an unmatched catch rate of malware and other types of attacks. Check Point offers a complete security architecture defending enterprises’ networks to mobile devices, in addition to the most comprehensive and intuitive security management. Check Point protects over 100,000 organizations of all sizes. At Check Point, we secure the future.
ABOUT CYSIGHT
CySight (cysight.ai) empowers security teams to safeguard critical assets across networks and clouds in the age of AI and encryption. CySight’s advanced AI-driven unified cybersecurity solution delivers 20x visibility and detection compared to others combined with enriched deep contextual insights, baselining, advanced threat detection, and a zero-trust approach identifying hidden threats such as infiltration, exfiltration, DDoS, ransomware, ToR, lateral movement, and insider threats for comprehensive protection of critical assets.
Worldwide Headquarters | 5 Ha’Solelim Street, Tel Aviv 67897, Israel | Tel: 972-3-753-4555 | Fax: 972-3-624-1100 | Email: [email protected]
U.S. Headquarters | 959 Skyway Road, Suite 300, San Carlos, CA 94070 | Tel: 800-429-4391; 650-628-2000 | Fax: 650-654-4233 | www.checkpoint.com.
CySight | Email: [email protected]
©2024 CySight Ltd and Check Point Software Technologies Ltd. All rights reserved. [Protected] Non-confidential content.
