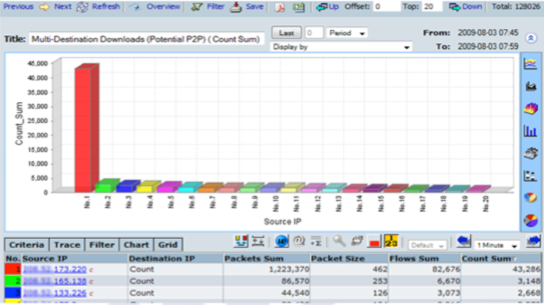
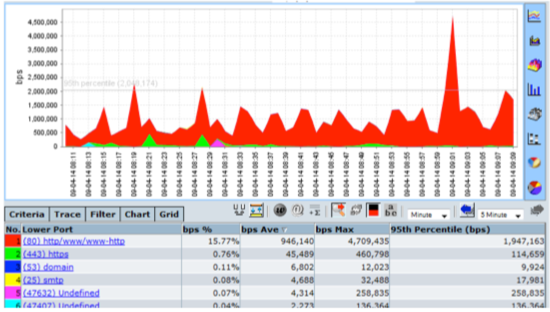
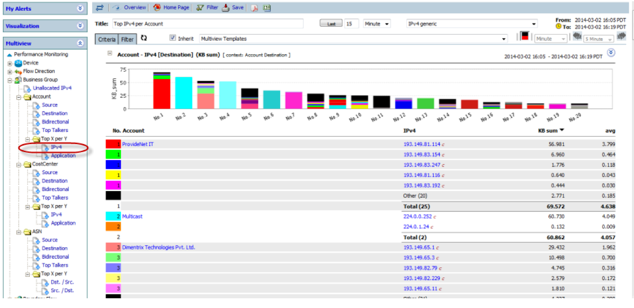
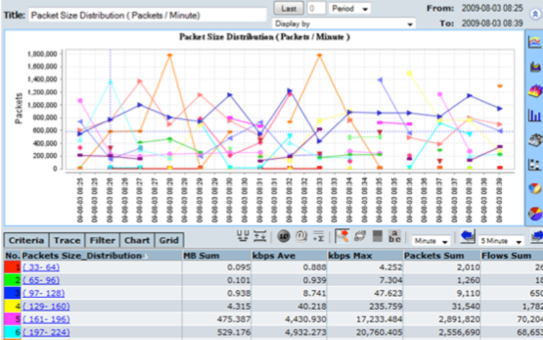
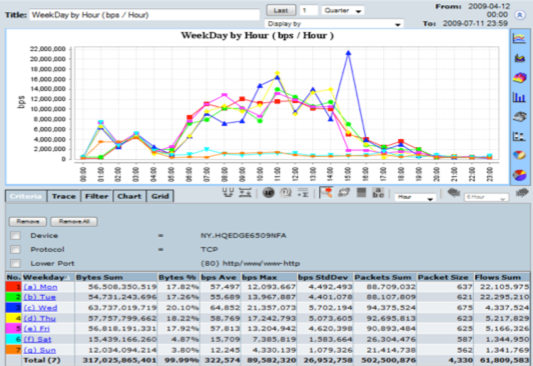
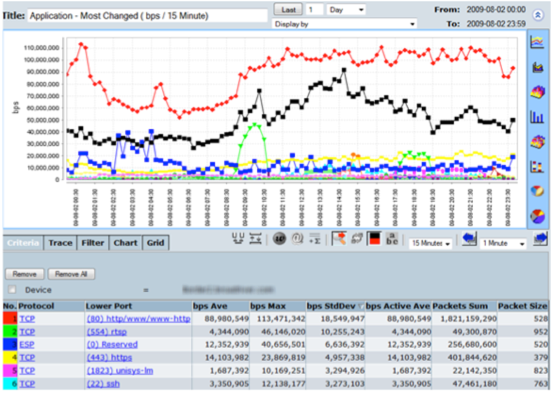
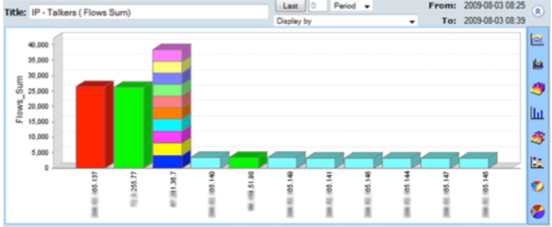
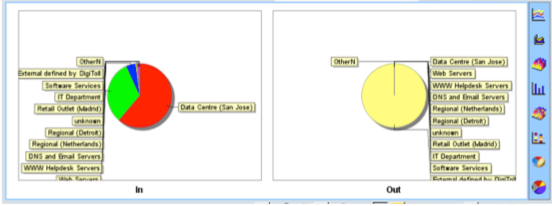
CySight provides visibility of every network conversation and scales beyond any other product in the industry.
Welcome to CySight, the solution that provides unparalleled visibility of every network conversation and scales beyond any other product in the industry. With the convergence of networks, increased data and network traffic volumes, heightened security vulnerabilities and threats, legislation and compliance issues, rising network costs, network performance demands, and stringent budgets, IT departments are faced with more challenges than ever before.
Open and complex networks have become increasingly more difficult to manage, and accountability and traceability of usage have become a necessity. The survival and competitiveness of organizations are reliant on the IT department’s success in largely mitigating the risk to the network, its performance, and its data through continual auditing.
At CySight, we understand these challenges and have developed a solution that addresses them effectively. Our solution enables organizations to perform network forensics for security at a granular level without depending on packet decryption, allowing security and network engineers to discover breaches of security that occur in real-time or those that occur over a prolonged period (data leaks).
Large networks generate copious amounts of Flow metadata that need a high degree of visibility to be scrutinized and reported on. While standard security devices (firewalls, intrusion detection systems, sniffers, etc.) may already be in place, they lack the ability to record and report on every transaction. Recording every transaction requires the ability to scale. Network flow data analysis, auditing, or forensic reporting at a granular level has been (until now) expensive and difficult to achieve and manage.
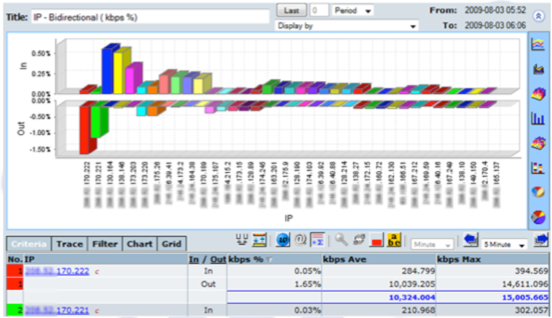
CySight offers a range of pre-configured forensics that provide multiple perspectives on network data, but it is not limited to these, and templates provide you the power to extend CySight. Our solution can perform analysis on any combination of data fields simultaneously (e.g. usage, packets, flows, packet size, utilization, latency, drops, counts, etc.) and sort data by any field. With our solution, you can effectively measure usage, trending patterns, baselines, averages, peaks and troughs, and standard deviations.
Menu bars and right-click drill-downs, baseline alerting, A.I. (Artificial Intelligence) Diagnostics, threat intelligence correlation, business grouping, automated reporting template shortcuts, and many other easy-to-use functions all facilitate in providing rapid analysis to effectively measure usage, trending patterns, baselines, averages, peaks and troughs, and standard deviations so that fast and appropriate action can be taken to reroute the packets that fit an attack profile.
What sets CySight apart from the competition is our unique ability to delivering SECaaS for multiple tenants or IPv4/6 groups at a compliance level of granularity. It leverages our unique ability to retain big data in a small footprint, threat triaging, integrated endpoint and behavioral detection, baselining and change detection, predictive AI, and AI diagnostics. With our solution, you have flexible deployment options – CySight can be deployed on-premises, in the cloud, or as a hybrid solution, giving organizations the flexibility to choose the deployment option that best fits their needs.
In addition, CySight helps organizations meet compliance requirements for regulations such as GDPR, HIPAA, and PCI-DSS. With CySight, organizations can start detecting and responding to threats in their network quickly, minimizing the time it takes to achieve value from their investment.
CySight’s advanced analytics and machine learning capabilities make it easy for security teams to hunt for threats and identify suspicious activity. Our solution provides real-time visibility into network traffic and endpoint activity, giving security teams the information they need to quickly detect and respond to threats. CySight provides a centralized management console that allows security teams to easily manage and monitor their entire security infrastructure from a single location.
CySight’s AI-Driven Network and Endpoint Threat Detection and Response solution provides several benefits for ISPs, MSPs, enterprises, and anyone who has a large data center or distributed global organization. These benefits include:
1. Improved Threat Detection and Response Time: CySight’s AI-driven analytics and machine learning algorithms can detect and respond to threats in real-time. This means that organizations can respond to potential security incidents quickly, minimizing the impact of cyber threats.
2. Enhanced Visibility: CySight provides comprehensive visibility into network and endpoint activity, even when traffic is encrypted. This means that organizations can detect and respond to potential threats that may otherwise go unnoticed.
3. Reduced Costs: CySight’s integrated solution reduces the cost of security by providing a comprehensive security solution that eliminates the need for multiple security tools. This reduces the overall cost of ownership and simplifies the security infrastructure.
4. Increased Operational Efficiency: CySight’s automated incident response and threat hunting features increase operational efficiency by reducing the time and effort required to detect and respond to potential threats.
5. Simplified Compliance: CySight’s compliance features ensure that organizations can meet industry regulations and standards, simplifying compliance efforts and reducing the risk of non-compliance penalties.
6. Scalability: CySight’s solution is scalable, making it ideal for organizations of all sizes. As the organization grows, CySight’s solution can easily scale to meet their evolving security needs.
7. Zero Trust Security: CySight’s integrated solution provides zero trust security by logically segmenting the network and enforcing access control policies. This ensures that only authorized users and devices can access sensitive data and resources.
8. Improved Incident Response: CySight’s granular forensics capabilities enable security teams to investigate security incidents quickly and accurately. This means that they can identify the root cause of the incident and take appropriate action to prevent similar incidents in the future.
9. Enhanced Threat Intelligence: CySight’s threat intelligence features provide real-time information about new and emerging threats. This information is automatically integrated into the security infrastructure, ensuring that organizations are always protected against the latest threats.
In summary, CySight’s AI-Driven Network and Endpoint Threat Detection and Response solution provides several benefits for organizations of all sizes. These benefits include improved threat detection and response time, enhanced visibility, reduced costs, increased operational efficiency, simplified compliance, scalability, zero trust security, improved incident response, and enhanced threat intelligence.