Solutions
CySight’s CySight is an integrated cyber network intelligence solution delivering scalable, granular on-demand, and actionable intelligence about everything traversing networks. Cyber and network intelligence modules are designed to run independently or work together as a powerful single unit. A highly scalable collection with unique granular retention delivers unprecedented network visibility.
CySight collects flow data from all kinds of flow-capable devices and cloud flow data providing the broadest vendor support in the industry. It can scale to huge flow feeds from large network cores and from hundreds of distributed physical or software-defined networking devices using conservative processing resources. It has the ability to extract deep intelligence enabling automated data-mining diagnostics delivering network teams and cyber hunters enhanced telemetry to quickly detect malicious traffic qualifying the seriousness of an anomalous network traffic event.
CySight’s flexible engine substantially cuts the time to integrate with 3rd Party partner tools to enable easy cross-analysis between complementary tools such as packet brokers, proxies, firewalls, and policy managers to deep-dive into packets or mitigate threats and anomalies discovered by CySight’s machine learning and diagnostic algorithms, without diverting massive volumes of data to scrubbing centers.
CySight Provides a broad and strategic “Base Layer” of Integrated Cyber Intelligence and Network Intelligence modules designed to run independently or work together as a powerful single unit bringing context to existing tools and enhancing Network management, Cyber Defense in Depth visibility, and IP Accounting.
The CySight unique capture methodology provides a ubiquitous collection of multi-faceted information from the network layer, the application layer, the data layer, and the perimeter layers that dramatically strengthens “defense in depth” and provides smart detection, intelligence, and unprecedented visibility to eliminate blind spots and quickly identify systems and infrastructure at risk substantially reducing the “mean time to know”.
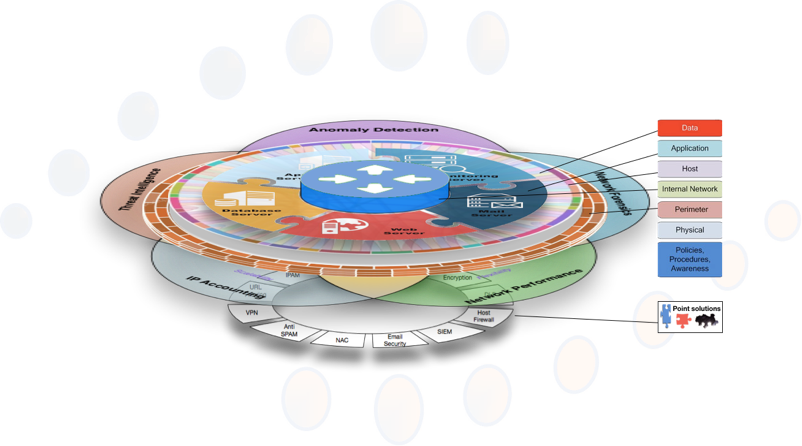
The intelligence that CySight derives is the glue that connects network, security, risk, architecture, applications and billing teams taking data feeds from the widest range of devices and functions to enable network and security professionals and existing tools to benefit from a single intelligent data source. No other solution can achieve broad coverage and unique granularity, scalability, flexibility, and intuitive forensics and cyber features at the same low cost, low impact, and easy deployment.
CySight is a unique and exceptionally powerful game-changing cost-effective solution that eases many pains in managing and securing complex network environments both on-premises and in the cloud.
Our unique granularity and scalability enable corporates, government and ISP’s to substantially improve efficiency and accuracy in identifying root causes, anomalies, and risks and account for every byte transferred using flexible machine learning traffic detection, intelligence, and forensics complying with Data Protection Laws and Retention Compliance.
Artificial intelligence analyzes, segments, and learns from granular telemetry from your network infrastructure flows in real-time using historical big-data for machine learning and threat intelligence correlation to identify cyber-threats and abnormal behavior otherwise undetectable. You can even discover encrypted traffic that is acting maliciously and has unprecedented visibility with comprehensive visual analytics and geo-mapping.
Our customers derive benefit from the depth, variety, and flexibility in analyzing and retaining network traffic that is unsurpassed. We are not owned by a networking vendor and are without vendor bias agnostically supporting all flow vendors and different kinds of networking equipment such as firewalls, routers, switches, Wi-Fi, packet brokers, and Cloud.
The growing complexity of the IT infrastructure is the major challenge faced by existing network management and security tools. Point solutions tend to cover a specialized aspect of what is going on inside the network and are severely handicapped because they lack the ability to provide the context of every transaction that is flowing across the network.
Requirements for flow analytics tend to fall into five main areas; Performance Analytics, Service Level Management, Cyber Security, Traffic Accounting, and Billing with various degrees of emphasis, and CySight uniquely provides access to one or more of these benefits from the smallest to the largest network environments.
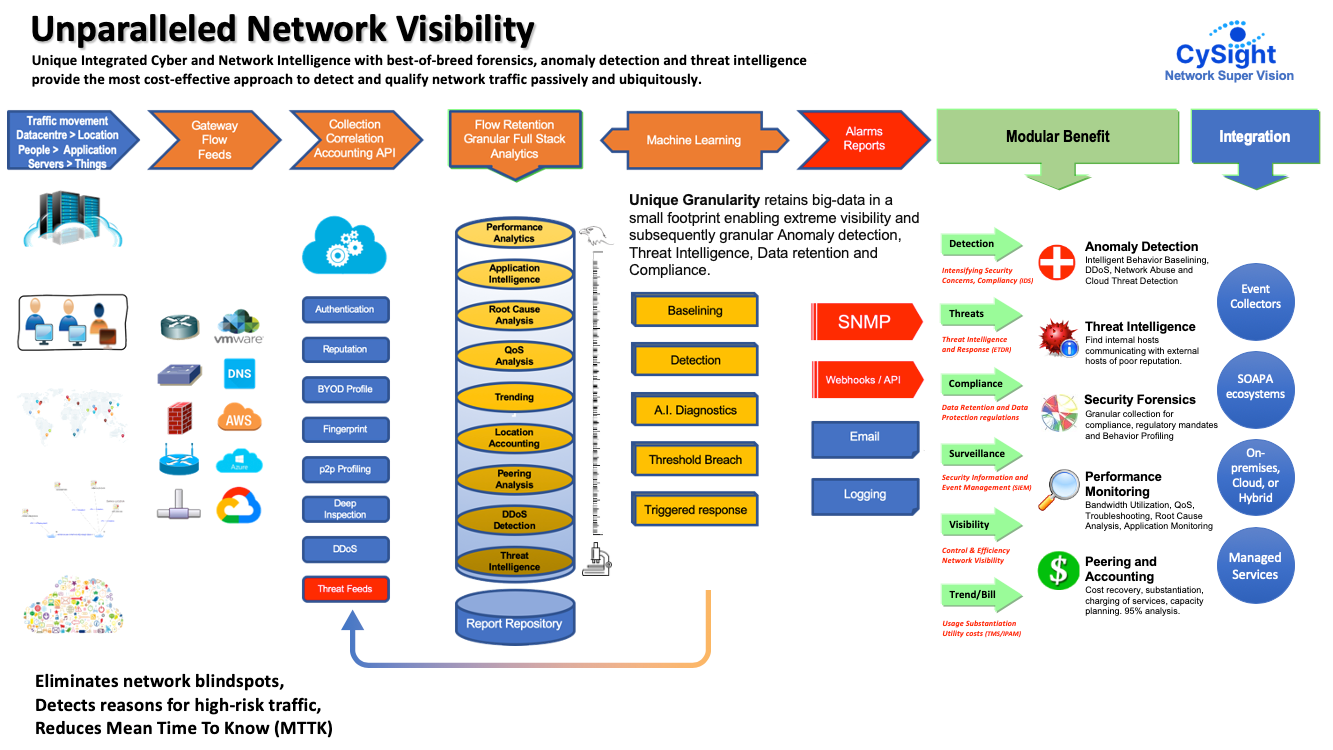
CySight’s unique Cyber Network Intelligence with best-of-breed forensics, anomaly detection, and threat intelligence provides the most cost-effective approach to detect and qualify network traffic passively and ubiquitously.
Engineering excellence delivers to you unsurpassed collection, correlation, granular data retention, and diagnostics that automatically extract deep intelligence from huge flow data to quickly detect threats, network misuse, and malicious traffic categorizing and qualifying the seriousness of an anomalous network traffic event. CySight was architected out-of-the-box to deliver;
- Granular Forensics for high visibility usually for deep Root Cause Analysis, Security and Data Retention Compliance,
- Intelligent Behavior Anomaly Detection for Discovery of traffic outliers and issues caused by attacks, abuse of bandwidth, DDoS/DoS, p2p, email spamming, and informative; e.g. video streaming and VoIP analytics,
- Threshold Alerting and Triggered Reporting for alerting on policy breaches, utilization breaches, and Application monitoring.
- Threat Intelligence: Monitor for communication end-points of poor reputation Correlates global threat big-data with real-time flows identifying risky conversations with Ransomware, Tor (onion routing), bitcoin mining, illicit traffic, malware, nefarious traffic and other traffic of ill repute.
- Scalable Performance Analytics for Bandwidth Utilization and Visibility,
- Accountable Billing/Trending to collect aggregated and 95th percentile usage stats for ROI by usage billing or trending of resource usage e.g. Month by month growth of interface/service/resource usage etc.
- Cloud Analytics for Amazon AWS and others
CySight scales in collection and retention well beyond any other solution. Additional flow collection tuning methods enable flows to be configured to match the organization’s policies or to comply with data retention compliance and privacy laws.
Our solution also scales in architecture and licensing and is therefore suitable for enterprises of any size. It is available for on-premise and cloud deployments. Multi-tenancy collection, portal, and automated reporting provide the ability to automate data-mining which can be integrated with upstream services and suits Managed Service providers (MSP’s) and Internet Service Providers and Telco (ISP’s) who are seeking to deliver advanced threat intelligence and network analytics.
It is comprised of multiple modules; Performance, Traffic Accounting, and Forensics; Machine Learning-based Anomaly Detection, and Automated A.I. Diagnostics; Threat Intelligence; Application Mapping, Correlation, and Flexible Templates; Visual Analytics; and Internet Protocol Address Management (IPAM) for Network Segmentation, Peering Analytics, and Billing. Standalone, clustering, hierarchical and multi-threaded collection provide flexible architectural options enabling cost-effective high compliance network traffic transaction logging with forensic analysis tools to perform data mining on any aspect of flow data from simple performance analytics to complex cyber-security profiling.
Machine Learning-based Anomaly Detection and Automated AI Diagnostics consists of a comprehensive Intrusion Detection System (IDS) comprised of machine learning, detection and artificial intelligence diagnostic engines that work together to find network behavior anomalies with automated problem-solving processes to pinpoint, mitigate and qualify the reason(s) for an anomaly.
Threat Intelligence based on global threat knowledge powers an advanced threat intelligence engine correlating, identifying, and detailing communications with nefarious endpoints in real-time that are known to be risky such as Ransomware, ToR, Botnets, Malware, and illicit p2p traffic.
Total Network Visibility
- Understand the impact of voice, viruses, hacking, multicast, DNS, peer-to-peer (P2P), and worms on your network.
- Proactively manage and troubleshoot network and application performance issues on even the largest of environments.
- Identify Bandwidth utilization and abuse and Justify bandwidth upgrades. Accurately plan network changes and new application roll-outs.
- Validate WAN Optimization schemes with pre-post deployment assessments.
- Monitor and managing service level agreements
- Ensure usage policies are enforced.
- Archive information for regulatory and compliance requirements.
- Analyze Peering traffic analysis
- Capacity Plan and forecast capacity requirements
- Pro-actively manage and troubleshoot network and application performance issues
- Reduce costs by substantially speeding up Mean Time To Repair (MTTR) and recovery using Automated Diagnostics and Comprehensive Traffic Accounting
Reduce Costs
- Implement charge-back and traffic accounting solutions.
- Enhance knowledge of internal data use and abuse.
- Take the guesswork out of capacity planning and substantiate upgrade costs with long-trending analysis.
- Substantiate business-related network traffic.
Increase Performance
- Identify network performance issues with comprehensive root cause analysis and forensics monitoring.
- Identify network gateway bottlenecks.
- Recognize and baseline actual use of key business services across cost centers.
- Plan for expansion of your company’s key business servers, data centers or whole of network needs.
- Monitor and alert on Service Levels with customized QoS values.
Protect Your Network
- Account for all traffic to key business services.
- Monitor compliance (sox; basel2, ISO) with long-term historical track and trace capabilities of all traffic to and from your key business systems.
- Identify unauthorized and inappropriate access.
- Identify spyware-infected computers.
- Automated reporting and alerting capabilities
