KEYSIGHT + CYSIGHT
AI-DRIVEN INTEGRATED CYBER VISIBILITY
Challenges Addressed
Enterprises face significant challenges in safeguarding their network and cloud connected digital assets in the age of encryption:
- Cyber Threats Identifying compromised hosts and abnormal behavior in communications between applications, hosts and endpoints seeking unauthorized network access or control over critical assets.
- Encryption Complexities Encryption’s rapid adoption globally complicates threat identification within data in motion, as over 98% of internet traffic is now encrypted, nullifying tools like Deep Packet Inspection (DPI) and leaving critical blind spots. Threat actors are using encryption to avoid detection.
- Visibility Gaps These visibility gaps obstruct security, challenging anomaly detection, risk identification, and swift response to cyber threats lurking within the network. Reliance on tools with limited capabilities that only surface-scrape data, encryption hindering data inspection, and segment orientated collection (such as DPI tools) prevent a complete view of network and cloud.
- Applications Intelligence This deficiency hampers the ability to accurately monitor, analyze, and secure critical application-centric activities, hindering effective threat detection and performance optimization.
- Compliance Complex IT environments struggle to maintain compliance standards amid evolving cyber threats and stringent regulatory constraints.
- Looming Risk The potential for adversaries to collect and exploit poorly encrypted data using Quantum decryption poses a looming risk.
The CySight + KeySight Joint Solution
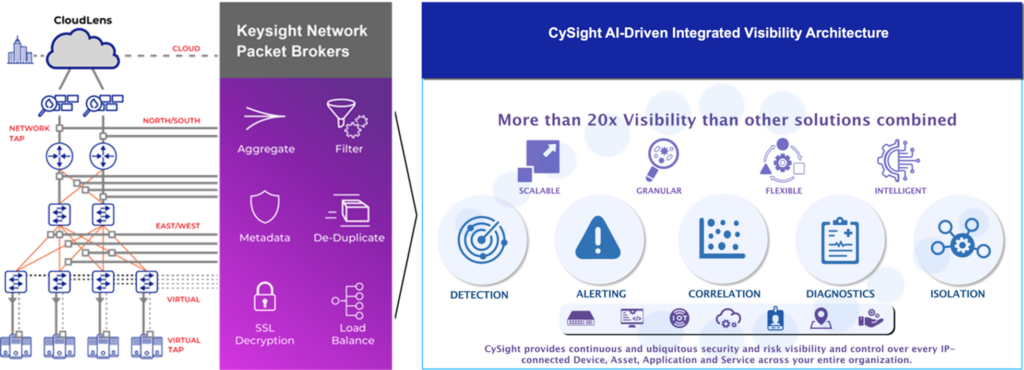
The integration of Keysight and CySight eliminates blind spots, providing unparalleled network and cloud visibility. It harnesses the robustness of Keysight’s enriched IxFlow and CySight’s AI-Driven Integrated Visibility Architecture for deep visibility of connected assets and baselines.
CySight ingests Enriched IxFlow from Keysight’s physical and virtual TAPs, Agents, and Packet Brokers and uses machine learning to detect change impacting hosts and services with total visibility, flexibility, and granularity. IxFlow amplifies CySight’s AI capabilities to enable swift identification of Cyber Threats concealed within encrypted traffic no matter how complex the networked environment.
Key Benefits of the
Integration
- Risk Detection from Analysis of IxFlow Enriched Metadata using CySight’s Scalable Collection and Deep Retention enabling high-resolution Machine Learning and AI Diagnostics.
- Eliminates visibility blind spots and is not constrained by granularity limitations.
- Granular, scalable, and actionable intelligence about everything traversing your network.
- Single solution for Anomaly Detection, Forensics, Threat Intelligence, Root cause Zero Trust and Network/Cloud Accountability.
CySight’s analysis of Keysight’s Enriched IxFlow provides comprehensive AI-Driven Cyber Security and Applications Intelligence by leveraging multiple enriched flows from both CySight and Keysight, offering deep insight into all the FLOWS.
SSL Analysis empowers customers to audit ciphers for vulnerabilities and to maintain control of certificate expiry dates. Ensure servers utilize quantum decryption resistant keys which is fundamental to mitigate future risks and fortify defenses against potential future threats.
SSH Unauthorized abnormal access patterns, access attempts or unusual SSH connections, reconnaissance or brute-force attacks originating from restricted locations can be readily identified and promptly addressed.
RADIUS Enables user authentication, authorization, and identification – assisting in the identification of vulnerabilities, ensuring enhanced security measures against unauthorized access attempts, and facilitating compliance adherence.
DHCP Enables discovery of irregular behaviors or suspicious activities within the network. The solution aids in detecting unauthorized devices or actors attempting to access the network.
EMAIL Leverages Keysight’s IxFlow for EMAIL analysis enables comprehensive scrutiny of email traffic. This analysis helps identify potential security threats such as phishing attempts or compliance breaches within email content, allowing for prompt action and risk mitigation
About CySight
CySight revolutionizes SecOps and NetOps through predictive AI baselining and unparalleled visibility across on-premise and cloud networks, coupled with robust deep forensics. Offering Actionable Insights and Business Intelligence from diverse network flows, CySight excels in collection, correlation, granular data retention, and AI-driven anomaly detection. Its advanced capabilities encompass machine learning, AI diagnostics, and global threat intelligence to extract critical insights from varied metadata sources, identifying threats and malicious activities, even within encrypted traffic. Trusted by Fortune 500 companies worldwide, CySight substantially reduces the cost of securing digital assets while delivering timely, precise monitoring information to the right teams at the right time.
https://cysight.ai
Learn more at: www.keysight.com
For more information on Keysight Technologies’ products, applications, or services, please contact your local Keysight office. The complete list is available at: www.keysight.com/find/contactus
