License Key Information
We know that each customer’s needs are different at different times and CySight, therefore, comes in scalable license tiers. A simple license change means that our customer’s investments are safe. So if your budget only allows a small start, we provide the very best small start in the industry and the ability to scale and grow as you need and add granularity and features.
CySight is designed for Corporations and Service Providers both small and huge. It is highly scalable and Telco grade.
Base License
- Performance provides granular troubleshooting top traffic information and retains high top granularity for as long as you need.
- Intelligence provides Performance granular troubleshooting top traffic information coupled with our unique long term data archive that can be tuned for your exact for trending, capacity planning, baselining and billing needs. Suits both small and large environments.
- Compliance is suited to those environments who require very granular collection for troubleshooting, security forensics and compliance. It is built to archive 100% of the flows and requires appropriate disk and processing resources.
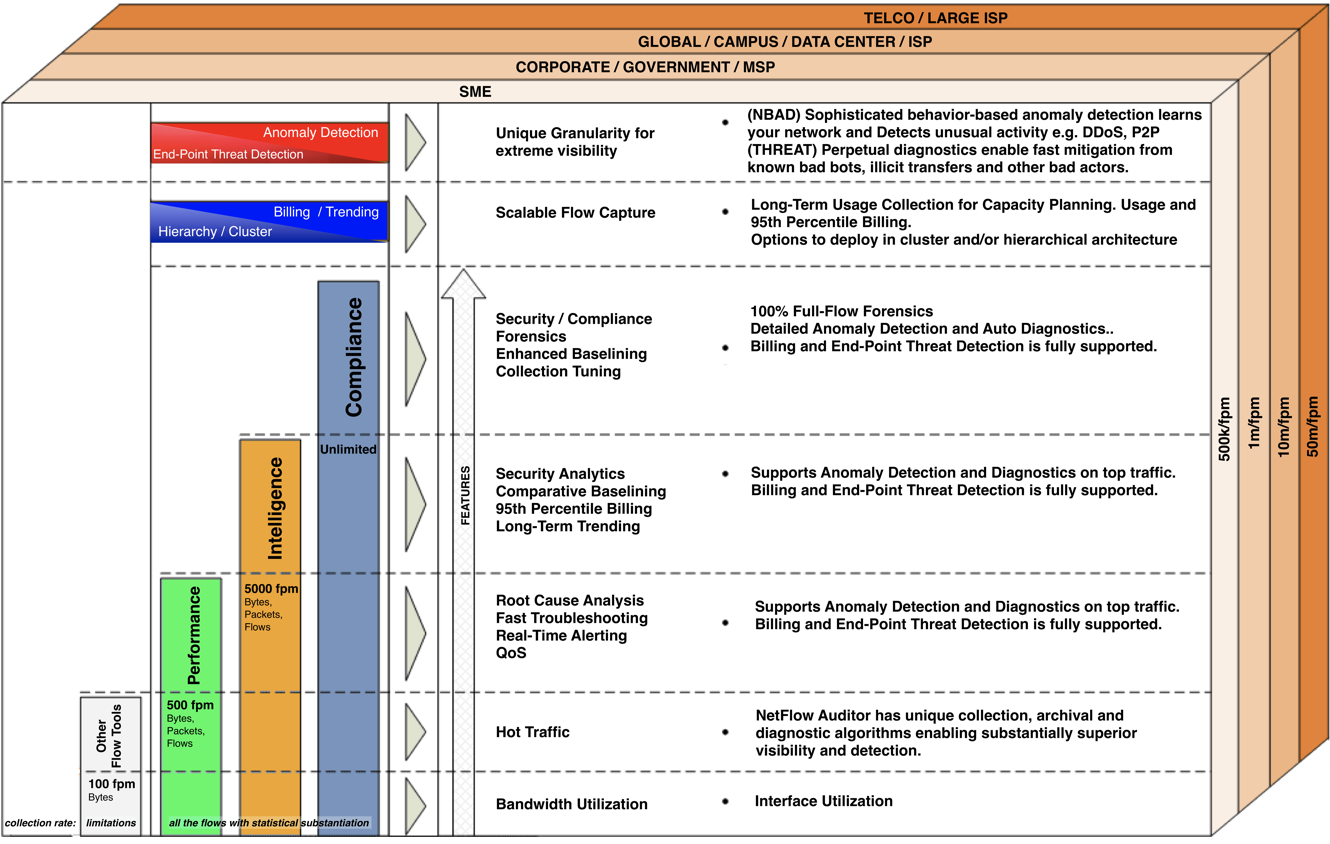
Cyber Security Add On Options
- Anomaly Detection (NBAD) license provides ability to automatically identify change (e.g. Intrusion Detection/Security/Compliance/Cost Management), Identify Nefarious Traffic, DDoS, SlowDoS, e-Vandalism. Detects threats and allows you to mitgate issues before they become bigger.Sensitivity can be retained as default for most environments and can be adjusted for special needs eg Defense/Banking/High Compliance.
- End-Point Threat Detection (THREAT) Perpetual diagnostics enable fast mitigation from DDoS, insider threats, botnets, illicit transfers and other bad actors.
Other Add On Options
- Ultra Long-Term Trending/Billing license provides ability to measure and analyze data in a separate data warehouse with tuning rules that allow for efficient and speedy long-term flexible baselining and comparative Predictive AI Baselining analytics and usage based or 95th percentile billing. Our unique long term data archive can be tuned for your exact for trending, capacity planning, baselining and billing needs.
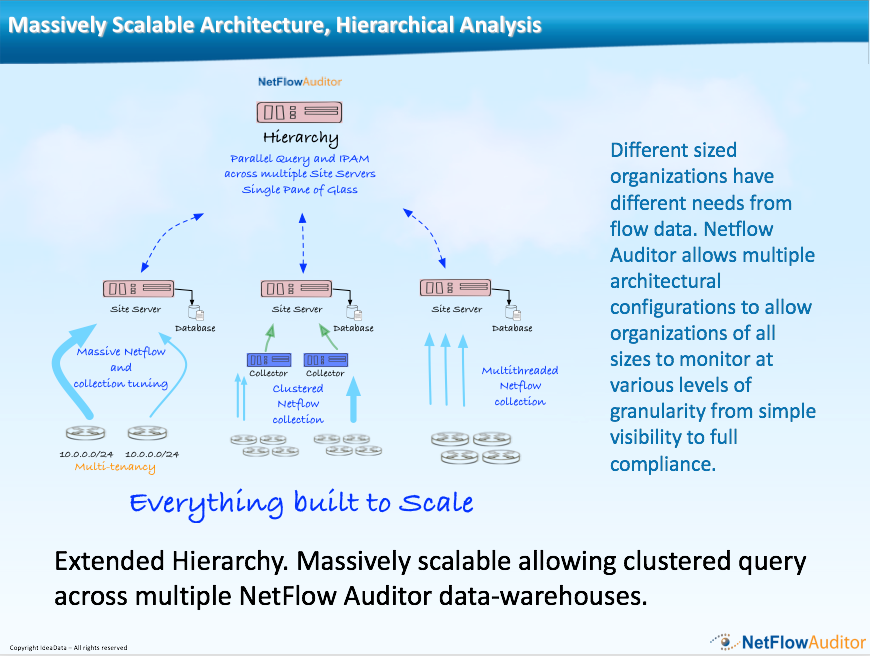
- Clustered/Helper Collectors allow CySight to be architected as a nfs cluster.
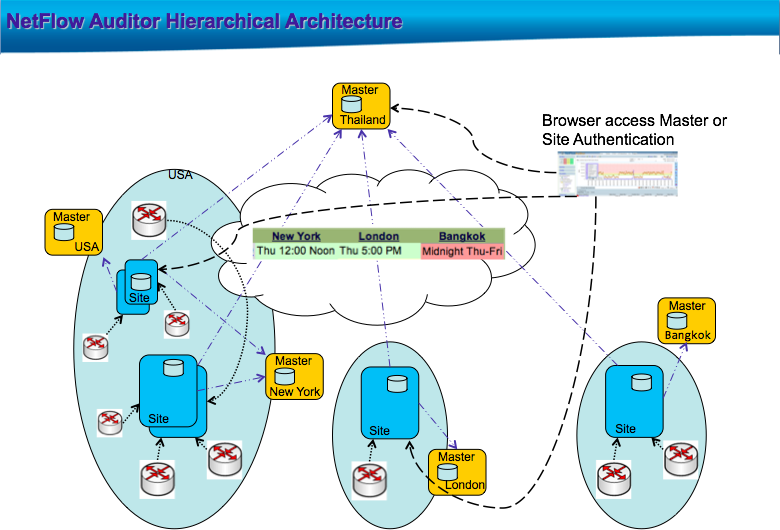
- Hierarchical Collectors allow CySight to be architected as a collection of distributed collectors that populate one or more hierarchical collectors for centralized awareness.
What is the Difference between CySight Performance, Intelligence, and Compliance?
To better understand the differences between CySight Base Licenses use this grid and the information below:
| Performance | Intelligence | Compliance | ||
| Base Config and Scaling | ||||
| Flow Collection Rate | Most granular, scalable and flexible Flow Collection in the industry. Provides hours, weeks months and years worth of data complete Auditing capability of every minute for security and performance needs or hourly long-term trending for capacity planning and system architecture needs. | 100% Raw Flow capture | 100% Raw Flow capture | 100% Raw Flow capture |
| Retention Rate (Archiving) | Dependent on license key limit. Potential Records per Device per minute is 500 for Performance, 5000 for Intelligence and not-limited for Compliance. Raw Flows subject to data collection Tuning or flow retention rate settings. | top talkers per device per minute default: 500 |
Intelligence: 5000 | Compliance: Unlimited and Configurable |
| Real-Time per Minute Data Archival | Unlimited | Unlimited | Unlimited | |
| Long-Term per Hour Data Archival | Ultra Long Term Trending / Billing Add-On | Optional | Optional | Optional |
| Baseline Real Time Comparison | Comparative analysis of each element across the time line. Gives the ability to identify which element caused the change and when. | Top Elements – months, week, weekday, day, hour, minute | Granular Top Elements Predictive AI Baselining analytics – week, weekday, day, hour, minute | Unlimited Granularity – week, weekday, day, hour, minute |
| Baseline Trending Comparison | Comparative analysis of Business defined elements across the time line e.g Accounts, Costcenters, Interfaces, Devices, ASN, QoS, Boundary, Protocol, Known Ports, 95th Percentile. Gives the ability to analyze resource growth needs, Bill for use by aggregation or 95th percentile. | years, quarters, months, week, weekday, day, hour, minute | years, quarters, months, week, weekday, day, hour, minute | years, quarters, months, week, weekday, day, hour, minute |
| Multi Device Support1 | Correlation and analysis of feeds from multiple appliances. Stand-alone, Cluster or Hierarchy Mode. Devices / Interfaces may be limited dependent on license tier. | Subject to license | Subject to license | Subject to license |
| Operating System Support2 | Windows or Redhat / Centos Linux | Windows or Redhat / Centos Linux | Windows or Redhat / Centos Linux | |
| Sustained flows / second1 | Subject to class of server (CPU, RAM, I/O, NIC), operating system, flow variance and number of devices and interfaces and flows per second collection tuning and flow retention license or rate setting CySight can collect upto to 10,000,000 flows/ second on single collector and millions of flows per second when scaled into a cluster or hierarchy. | Avg 1500000 flows/ second sustained or 5 million flows per second burst subject to flow variance, | Avg 300000 to 1500000 flows/ second sustained subject to flow variance. | At full retention setting 30000 flows/ second sustained or 100000 burst or 300000 fps subject to flow variance |
| Fault tolerant and scalable collection | CySight was built from the ground up for scalability and utilizes scalable intelligent agent technologies (Bots) to manage large amounts of network traffic information in real time. | yes | yes | yes |
| Data Collection Tuning | Collect only the data required. CySight provides strategic data collection tuning allowing inclusion / exclusion for collection and additional scalability | yes | yes | yes |
| Health Check | Monitors the overall network health and export loss statistics. | yes | yes | yes |
| Flow Capture | ||||
| NetFlow | Captures Cisco NetFlow Data v1,5,7,9 and Flexible Netflow and flows from Cisco ASA, Nexus, ASR, Cisco WLC, CheckPoint, Ixia, Juniper, Palo Alta, Brocade, Microtik and many more | yes | yes | yes |
| IPFIX | Captures IPFIX data | yes | yes | yes |
| sFlow | Captures sFlow (4.0.2 onward) | yes | yes | yes |
| sFlow | Captures jFlow, NetStream, VMware | yes | yes | yes |
| CySight Base architecture | ||||
| Flexible multi-option filtering Analysis | Packet Size, Full Flow, Count, Deviation, Bidirectional, Cross sectional and Business group analysis. | top | granular top | all |
| Scalability, Fault Tolerance and Self Healing | Architected using Intelligent Agent Technology | yes | yes | yes |
| User Profiles | Customizable login environment for each account with Predictive AI Baselining analytics for IP Owner to only view their Subnet or Device | yes | yes | yes |
| Hierachical Collection | License based on number of Collectors monitored | yes | yes | yes |
| Scheduled Reports, Alerting and Templates | ||||
| Unattended Analysis | Alerting and Reporting or create drilldown templates for quick analysis of your specific needs. | top | granular top | all |
| Anomaly Detection Alerting | Optional Add-on license based on active device license. Exception and/or threshold alerts on a wider range of events rising or dropping traffic to particular end point, rising/dropping protocol to end point, idle period to end point, standard deviations, network behavior anomaly detection baselines for each Measurement Profile Flows / bps / pps / Packets / Packet Size / Bytes / Counts / TCP Flags + Congestion Flags (8). A Minimum of 11424 Intelligent Baseline Statistics are learned for each Monitored Traffic Item. (4 Statistical baselines for each of the 17 Measurement Profiles for each hour for each weekday). |
Outliers primarily bandwidth usage orientated | Outlier detection is granular and sufficient for most ernvironments | Full detection and automated Predictive AI Baselining analytics is able to use all the data for Machine Learning |
| Intelligent Baseline Learning | optional | optional | optional | |
| Scheduled Reporting | Custom NetFlow Reports can be scheduled to run as a report. | yes | yes | yes |
| Standard Alerting | Custom NetFlow Reports can be scheduled to run as a standard alert. | yes | yes | yes |
| Templates | Custom NetFlow Reports can be saved as a Drilldown Template | yes | yes | yes |
| Standard Alerting | Ability to set global real-time alerting thresholds based on changes in volume, destination, source or port and Time of day event alerting and thresholds | yes | yes | yes |
| SNMP traps | yes | yes | yes | |
| SNMP v3 Support | yes | yes | yes | |
| Email Delivery | PDF, CSV. HTML. | yes | yes | yes |
| Report Repository | PDF, CSV. HTML. | yes | yes | yes |
| On Demand Delivery | PDF, CSV | yes | yes | yes |
| DDoS discovery | limited | substantial | complete | |
| P2P discovery | limited | substantial | complete | |
| ICMP floods discovery | limited | substantial | complete | |
| Nefarious traffic discovery | limited | substantial | complete | |
| Filtering and Display | ||||
| 100% Flow Capture Analysis | Reports on which hosts, applications, protocols, etc. are using the least network traffic. | no | no | yes |
| Top Analysis | Reports on which hosts, applications, protocols, etc. are using the most network traffic. | yes | yes | yes |
| Flexible Filters | Allow you to include or exclude any aspect of the flows to design exactly the report you need | yes | yes | yes |
| Menu bars and shortcuts | Facilitate rapid analysis. | yes | yes | yes |
| Data Collection Tuning | Ability to apply filters when performing a packet capture. | yes | yes | yes |
| Business / Location based Grouping | Location based on specific pre-defined groups for target IP ranges. Used in conjunction with billing trending add-on provides fast 95th percentile and usage reports that can be delivered in csv format for easy integration into existing billing systems. | yes | yes | yes |
| Interface Analysis | All interfaces can be analyzed regardless of flow limits | yes | yes | yes |
| Application based Grouping | Application based on specific pre-defined groups or targets. | top | all | all |
| Built in One-Click Capacity Planning | Long-term Baseline trending. Compare any aspect over years, quarters, months | Optional | Optional | Optional |
| AS Number reporting | all | all | all | |
| QoS analysis | all | all | all | |
| Bidirectional Analysis | interface | full | full | |
| Multi-path Deduplication | Exclusion reports provide automated ability to remove duplication when analyzing multiple routers or switches. | top | all – subject to data availability | all |
| Ingress/Egress Deduplication | Detailed information when looking at a single device with multiple interfaces with ingress and egress enabled will de-duplicate when using v9 Flexible Netflow | top | all – subject to data availability | all |
| Packet size distribution | top | granular top | all | |
| Route Path Analysis through multiple devices | top | all | all | |
| Search for hosts or applications | Across hundreds of routers/ switches. | top | all – subject to data availability | all |
| Device Grouping | all | all | all | |
| Interface Grouping | all | all | all | |
| Location Grouping | all | all | all | |
| Subnet Grouping | all | all | all | |
| 95th Percentile | Ability to create 95th Percentile (Or any percentile) for any measurement such as bps, packets, Extensive chargeback information – Provides byte, flow, packet counting and 95th percentile information from the interface down to the smallest addressable network unit or user. Enables complete flexibility on the combination of elements to be used for chargeback including Network AS, IP address, Ports, Applications, Locations or QoS. Providers can differentiate pricing based on time periods, server, content or route. | top | partial | full |
| True 95th Percentile billing1 | top or interface only | partial | optional | |
| Graph Types | ||||
| Timeline | yes | yes | yes | |
| Timeline Extensive | Full comparative analysis of each element across the time line | top | granular top | yes |
| Stacked Area | yes | yes | yes | |
| Stacked Area Extensive | Full analysis including no flow periods | top | granular top | yes |
| Bar | yes | yes | yes | |
| Pie | yes | yes | yes | |
| Stacked Bar | yes | yes | yes | |
| Visual Analytics | Analyze by any orientation Bytes, Flows, Packets, Packet Size, TCP Flags, pps, Latency, Drops or any other measure available | |||
| Sankey | Flexible Sankey graphing allows relationship Predictive AI Baselining analytics for any number of dimensions. Sankeys can be built directly from an existing Forensic | yes | yes | yes |
| Geo-Location Topology | Auto Geo Location of every IPv4 Address on drillable world map with interface orientation option. Topology is available for IPv4, Interfaces, Country and Regions | yes | yes | yes |
| Chord | Indicates top N in a circular point to point analytic. Includes size of Measure. | yes | yes | yes |
| Bundle | Indicates top N in a circular point to point analytic without bandwidth using up chart real-estate. | yes | yes | yes |
| Force Graphs/Connected Topology | Indicates connected relationship between objects. The distance between the objects reflects the strong/weak connectivity. Force graphs are available for Interfaces, Accounts, Costcenters, ASN and IP Addresses | yes | yes | yes |
