Consume metadata at scale. Retain the granularity that forensics requires.
CySight captures, normalizes, enriches, and retains high volume context and metadata and flow across vendors and environments. Investigate encrypted and segmented networks without relying on packet decryption, including slow burn leaks and long running breaches.
Security grade visibility without the cost and complexity
Large environments generate massive volumes of flow metadata. Traditional approaches either miss most of it or become too expensive to retain, search, and explain. CySight is designed to retain big data in a small footprint and keep the granularity that real investigations, compliance, and accountability require.
Collect flow metadata across vendors and distributed environments, including high rate collectors. Keep what the device provides, then standardize it so analytics stay consistent.
- High volume ingestion, multi tenant, IPv4 and IPv6
- Consistent normalized fields for comparable analytics
- Long term retention without discarding fidelity
Learn identities from sources such as RADIUS and LDAP, and from tools that integrate with them and provide APIs. Apply learned identity context across conversations to strengthen triage and accountability.
- User and device attribution for investigation
- Consistent identity labels across time ranges
- Supports deeper context where available
Geo and regional attribution is a default lens for triage. If additional regional context is added, it increases clarity and speeds prioritization. This strengthens conclusions without requiring payload inspection.
- Fast triage by country, region, and boundary
- Clearer prioritization for suspicious patterns
- Supports segmentation and accountability
Connect the dots across assets, identities, applications, peers, threats, and events. Use the vector store to extend relationship discovery and continuously improve investigation quality as CySight lands and expands.
- Lateral connectivity across learned contexts
- Joined context for faster investigation and reporting
- Designed to extend as new sources are integrated
Baselining is not separate from forensics. CySight uses behavioral baselines to generate events, discover deviation, and triage what matters. Events carry quantified context to support clear decisions and audit trails.
- Event driven forensics with evidence
- Quantified change across time windows
- Supports lateral movement discovery
Zero Trust is strengthened when risk is measurable and traceable. CySight quantifies risk in events, then feeds joined context and vector connectivity back into the detection cycle to keep baselines and triage sharp.
- Risk tracked across multiple impacts
- Clear accountability by asset, identity, and boundary
- Evidence supports compliance and insurance narratives
Core forensic lenses
These lenses are designed for speed, clarity, and long term traceability. Combine them across any field set and any time range, then pivot instantly to explain what changed, who was impacted, and what the evidence shows.
Supported flow structures
CySight supports multiple flow structures across vendors and environments. Each structure includes a defined field set, normalized mappings, and extension points for enrichment and joined context.
CySight Stack reference
The CySight stack is the operating model for security, IT, and compliance teams: collection, normalization, enrichment, AI baselining, threat correlation, forensics, and response workflows.
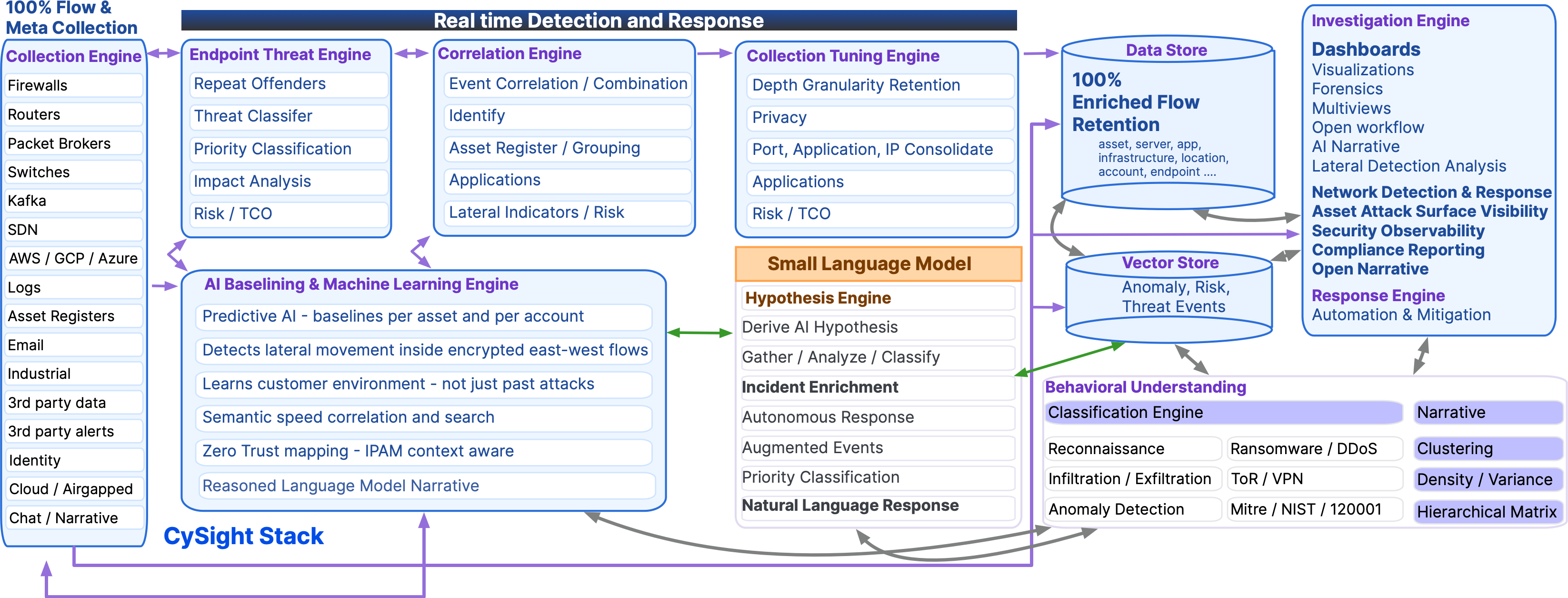
- Collect flow and log metadata at volume, across vendors and environments
- Normalize into consistent structures so analysis stays comparable
- Enrich with identity, geo, threat intelligence, and business context
- Baseline every asset and service behavior to detect drift and covert patterns
- Investigate with forensic lenses built for speed and long term traceability
- Respond by exporting evidence and alerts to your policy manager, XDR, or SIEM
Proof in the UI
The forensics experience is designed to match the strength of Threat, Baseline, and Performance views. The Daashboard and UI is where joined context, event triage, and rapid drill down become operational.
High density forensics view designed for investigation speed: entities, ports, deviation, snapshots, direction, boundary, and event category.
Joined context view that brings together groups, assets, services, countries, and external IPs, with event driven exploration and rapid triage.
- AI event baselining and discovery that produces investigation ready events
- Joined contexts that connect identity, asset, geo, threat, and business grouping
- Zero Trust lens that tracks boundary behavior and accountability across time
- Vector lateral connectivity that reveals relationships and movement paths
- Quantified risk recorded in events, then fed back into the detection cycle