Your network has already, or soon will, be infiltrated
To win the war on cyber extortion, you must first have visibility into your network and it is imperative to have the intelligent context to be able to find threats inside your data
Ransomware has become the most prevalent Trojan but other Trojans such as Spyware, Adware, Scareware, Malware, Worms, Viruses, and Phishing all play a role in delivering Ransomware to your Network, Server, Laptop, Phone, or IoT device and can in their own right be damaging.
CySight hunts them all, but in this article, OUR FOCUS IS ON RANSOMWARE and how to try to identify it before it causes financial and social damages.
Given what we already know and that more is still being learned, it makes good sense to investigate our unique solution.
What Is the Impact of Ransomware?
It’s not just your home laptop at risk, entire Enterprises can and are being held at Ransom – e.g. NotPetya Ransomware attack on Maersk required full re-install of 4000 servers, which they announced resulted in a loss of $300 million.
The spread and popularity of Ransomware, which is up from $11.5B in 2019 to $20B in 2020 and still rising, is outgrowing legacy solutions that cannot identify zero-day infiltration, at-risk interconnected systems, and related data exfiltration.
Attacks are set to have huge growth in 2021 and beyond!
The Ransomware Protection Racket?
Ransomware can be like the old analog world protection racket :
- You pay once, but they’ll come back later asking for more.
- You might pay but never get your data back.
- They could give you the decryption key to get your data back, but sell the key to other hackers along with your corporate secrets.
- They understand the value of reputation and wanting to keep breaches private.
- They’ll go after especially important and critical infrastructure and services.
- It is not just the enterprise that is at risk, but the interconnected components like ISPs and BYO personal devices.
- The bigger you are the more the hackers think they can get and will try to!
A single infection could cost an organization thousands of dollars. (or millions!)

Evolved “double extortion”
It is important to take cognizance of the rise of double extortion attacks as criminals have come to realize that encrypting your files and stipulating a ransom to get back access to your data may be mitigated by backup strategies.
Decryption keys are good for business!
Like any good Protection Racket, Ransomware criminals understand that in order to make money they need to establish a certain decorum. By ensuring a customer can get a key to decrypt after paying the ransom they build a level of “trust” that it just takes money to get your files back. Pricing is usually set at a level where the Ransomer feels they can extract payment at the level the ransomed can afford. This allows continuity and repeat business.
When not paid impact reputation.
Hackers have also become experts in the art of Doxing which means gathering sensitive information about a target company or person and threatening to make it public if their terms are not met.
This has been a strategy for some time but it is becoming more prevalent for an attacker to exfiltrate a copy of the data as well as encrypting them and in that way prevents access to your data as well as having to be able to leverage your sensitive information going well beyond the simple lock and key protection racket and taking extortionware to a whole new level which can create years of ongoing demands.
Infrastructure, key servers, critical services.
As Ransomware progresses it will continue to exploit weaknesses in Infrastructures. Often those most vulnerable are those who believe they have the visibility to detect.
Ransomware is a long game often requiring other trojans or delivery methods to slowly infiltrate corporations of all types. They sleep, waiting for the right time to be activated when you least expect it.
ISP / Corporate / Industrial / SMB / Person
There are literally hundreds of ransomware variants targeted to both huge and sensitive corporate or government infrastructures that activate and encrypt on botnet instruction or when a set of circumstances activates the algorithms. They make use of payment gateways that are almost impossible to break and track.
It’s not all doom and gloom if you catch it early, it makes good sense to investigate our unique solution.
Threat Hunting (Ransomware)
The Postmortem Snowball Impacts!
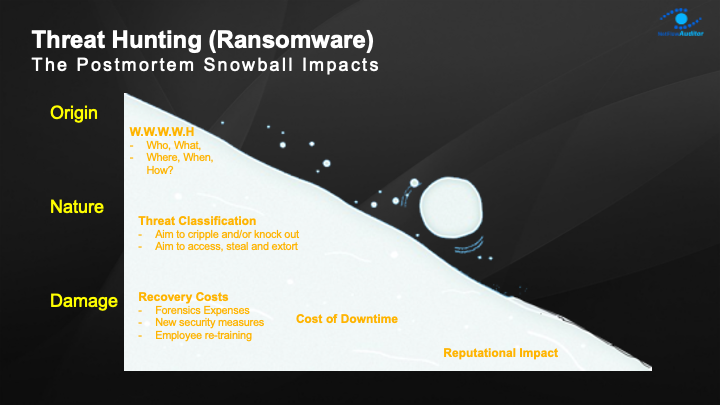
When hunting for Ransomware there is often a snowball-like effect in terms of effort and impact.
You might start looking to answer questions like where the Ransomware came from, who did it, when did it happen, is there a patch to protect in future etc.
But you need to know more detail than that to judge your response;
- The nature and classification of the threats are vital to know. e.g. is it scareware with no real impact? are they just trying to sell lousy protection software? Or is it real criminal intent and your data will be gone?
- How serious is the Damage are we talking about and how widely has the problem spread?
- What’s the cost to operations?
- If you don’t remediate or pay, what the less quantifiable but very important reputation impact to your business?
- After the fact, what employee re-training is needed?

- What is the mindset of your Security organization?
- Do they have all the traditional enterprise security measures in place and are ‘Certain’ they know everything (this is the worst-case scenario.)
- Or are they aware of their ‘Limited’ ability to find ransomware, but don’t have the time or tools to deal with it.
- Do they rely on backups, updates, and patching, which are also good practices but insufficient?
- What if the hackers encrypt your backup drives?
- Is the organization deluded are they ‘aware’ or understand they are ‘blind’
Answering all these questions takes more and more time and costly manpower, especially if you lack the tools to effectively undertake such threat hunting.
IN THE CURRENT INFECTIOUS CLIMATE WE’VE ALL BECOME SO SENSITIZED TO THE FACT THAT THE TINY RANSOMWARE AND TROJANS THAT WE DON’T SEE CAN POSE THE BIGGEST THREATS AND INVISIBLE DANGERS!
Deep insight into the granular nature of how systems, people process, applications, and things have communicated and are communicating is critical. In our attempts to discover hidden threats we need to deploy granular tools to collect, monitor, and make known the invisible dangers that can have real-world impacts.
It often overlooked but it is not a secret that in even well-known tools have serious shortcomings and are limited in their ability to retain complete records. They don’t really land up providing the visibility of the blindspots they alluded to. In fact, we found that in medium to large networking environments over 95% of network and cyber visibility tools struggle to retain as little as 2% to 5% of all information collected and this results in completely missed diagnostics, severely misleading analytics that cause misdiagnosis and risk!
YOU DON’T KNOW WHAT YOU DON’T KNOW!
AND IT’S WHAT WE DON’T SEE THAT POSES THE BIGGEST THREATS AND INVISIBLE DANGERS!
You may be surprised to learn that most tools lack the REAL Visibility that could have prevented attacks on a network and its local and cloud-connected assets. There are some serious shortcomings in the base designs of other flow solutions that result in their inability to scale in retention. This is why smart analysts are realizing that Threat Intelligence and Flow Analytics today are all about having access to long-term granular intelligence.
From a forensics perspective, you would appreciate that you can only analyze the data you retain, and with large and growing network and cloud data flows most tools (regardless of their marketing claims) actually cannot scale in retention and choose to drop records in lieu of what they believe is salient data.
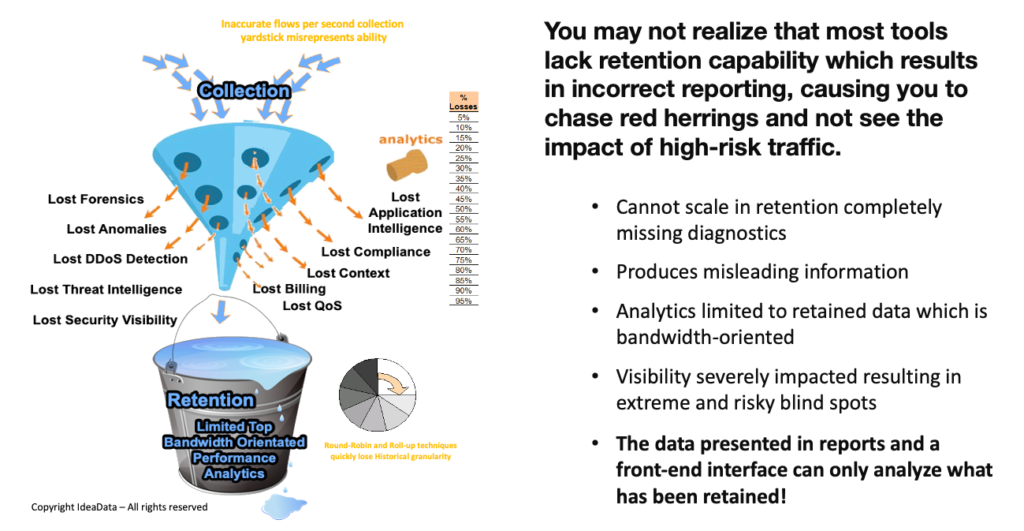
Imputed outcome data leads to misleading results and missing data causes high risk and loss!
Big Data is heavy to store and lift.
We have seen many engineers try to build scripts to try to attain the missing visibility and do a lot of heavy lifting and then finally come to the realization that no matter how much lifting you do that if the data is not retained then you simply cannot analyze it.
Don’t get me wrong, we love the multitude of point solutions in our market that each tries to address a specific need – and there are a lot of them. DDoS detectors, End-Point threat discovery, Performance management, Email phishing detectors, Deep Packet Inspectors, and more.
DPI is a great concept but It is well known that Deep Packet Inspection (DPI) solutions struggle to maintain both a heavy traffic load and information extraction. They force customers to choose one or the other.
Each of these tools in their own right has value but they are difficult and expensive to integrate, maintain and train.
The data sources are often the same so using the right tool and an integrated approach for flow data allows SecOps, NetOps to reduce the cost overheads of maintaining multiple products and multiplies the value of each component.
Smart analysts are realizing that combining Network and Cyber Intelligence using Flow management today with the capability to access long-term granular intelligence is a seriously powerful enabler and a real game-changer when detecting Ransomware and finding exfiltration and related at-risk systems.
So how exactly do you go about turbocharging your Flow and Cloud metadata?
Our approach with CySight focuses on solving Cyber and Network Visibility using granular Collection and Retention with machine learning and A.I.
CySight was designed from the ground up with specialized metadata collection and retention techniques thereby solving the issues of archiving huge flow feeds in the smallest footprint and the highest granularity available in the marketplace.
Network issues are broad and diverse and can occur from many points of entry, both external and internal. The network may be used to download or host illicit materials and leak intellectual property. Additionally, ransomware and other cyber-attacks continue to impact businesses. So you need both machine learning and End-Point threats to provide a complete view of risk.
The Idea of flow-based analytics is simple yet potentially the most powerful tool to find ransomware and other network and cloud issues. All the footprints of all communications are sent in the flow data and given the right tools you could retain all the evidence of an attack or infiltration or exfiltration.
However, not all flow analytic solutions are created equal and due to the inability to scale in retention the Netflow Ideal becomes unattainable. For a recently discovered Ransomware or Trojan, such as “Wannacry”, it is helpful to see if it’s been active in the past and when it started.
Another important aspect is having the context to be able to analyze all the related traffic to identify concurrent exfiltration of an organization’s Intellectual Property and to quantify and mediate the risk. Threat hunting for RANSOMWARE requires multi-focal analysis at a granular level that simply cannot be attained by sampling methods. It does little good to be alerted to a possible threat without having the detail to understand context and impact. The Hacker who has control of your system will likely install multiple back-doors on various interrelated systems so they can return when you are off guard.
CySight Turbocharges Flow and Cloud analytics for SecOps and NetOps
As with all CySight analytics and detection, you don’t have to do any heavy lifting. We do it all for you!
There is no need to create or maintain special groups with Ransomware or other endpoints of ill-repute. Every CySight instance is built to keep itself aware of new threats that are automatically downloaded in a secure pipe from our Threat Intelligence qualification engine that collects, collates, and categorizes threats from around the globe or from partner threat feeds.
CySight Identifies your systems conversing with Bad Actors and allows you to backtrack through historical data to see how long it’s been going on.
Summary
CySight software is capable of the highest level of granularity, scalability, and flexibility available in the network and cloud flow metadata market and supports the broadest range of flow-capable vendors and flow logs.CySight’s Intelligent Visibility, Dropless Collection, automation, and machine intelligence reduce the heavy lifting in alerting, auditing, and discovering your network making performance analytics, anomaly detection, threat intelligence, forensics, compliance, and IP accounting a breeze!
Let us help you today.